Online access to your favorite apps was never more secure than it is now, but you may still want an assurance that no one else has hacked into them. This can be difficult if those websites use only basic security measures like SSL certificates and passwords for user accounts.

WhiteHat’s 2017 application security statistics report found 30% of total breaches involved attacks on web apps which means they often lack many other important protections such as firewalls or anti-malware programs. This makes understanding how trustworthy each provider is important before signing up with any company offering app security services. To assess your app’s security status, you can turn to either source code review or penetration testing.
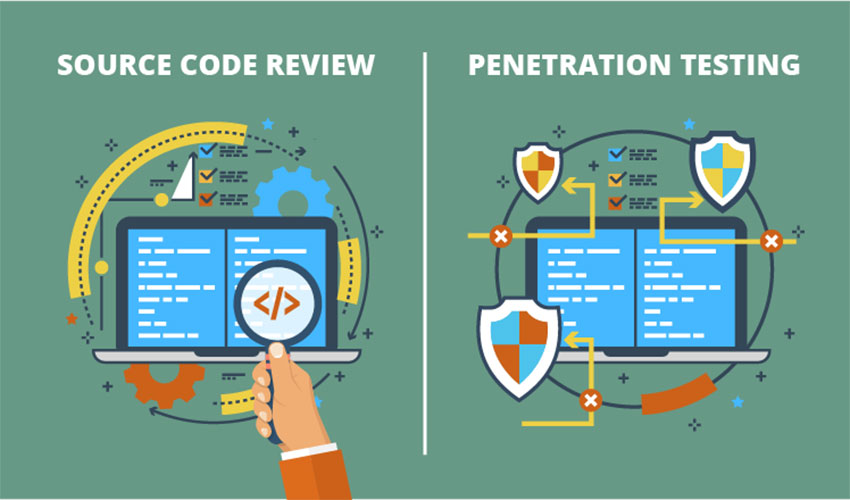
But what exactly do they involve? Which method will identify more flaws and provide you with accurate information about the security of your app and team? What will provide you with the best return on your investment? Let us investigate these two approaches one by one.
Understanding Source Code Review
Source Code Review testing method directly analyses source code and exposes errors that were overlooked during the initial development phase. It is the process of auditing an application’s source code to ensure that the appropriate security controls are present, their functions are as intended, and they have been invoked in all the right places. Code review ensures that the application has been designed to be self-defending in its particular environment.
“Secure code review is probably the simplest effective technique for identifying security bugs early in the development process. When used in conjunction with automatic and manual intrusion tests, code review can significantly increase the effectiveness of verifying application security.”
What are the Major Benefits of using Source Code Review for web development?
- Source Code Analysis is integrated into the development process, which saves time and money.
- Extremely user-friendly, easy to set up, and personalize.
- Reduces reliance on the programmer’s ability to write secure code.
- Very effective at detecting XSS and SQL Injection errors.
- It can also be used for quality assurance and overall product improvement.
Understanding The Penetration of Testing web application development
A penetration test simulates a cyber attack on your computer system in order to identify exploitable vulnerabilities. Penetration testing is often used to supplement a web application firewall in the context of web application development security. Pen testing entails attempting to breach any number of application systems to discover vulnerabilities such as unsensitized inputs that are vulnerable to code injection attacks.
“Only 52% of IT professionals are proactive in addressing security concerns before a breach happens.”
The results of the penetration test can be used to fine-tune your web application firewall security policies and patch any vulnerabilities discovered.
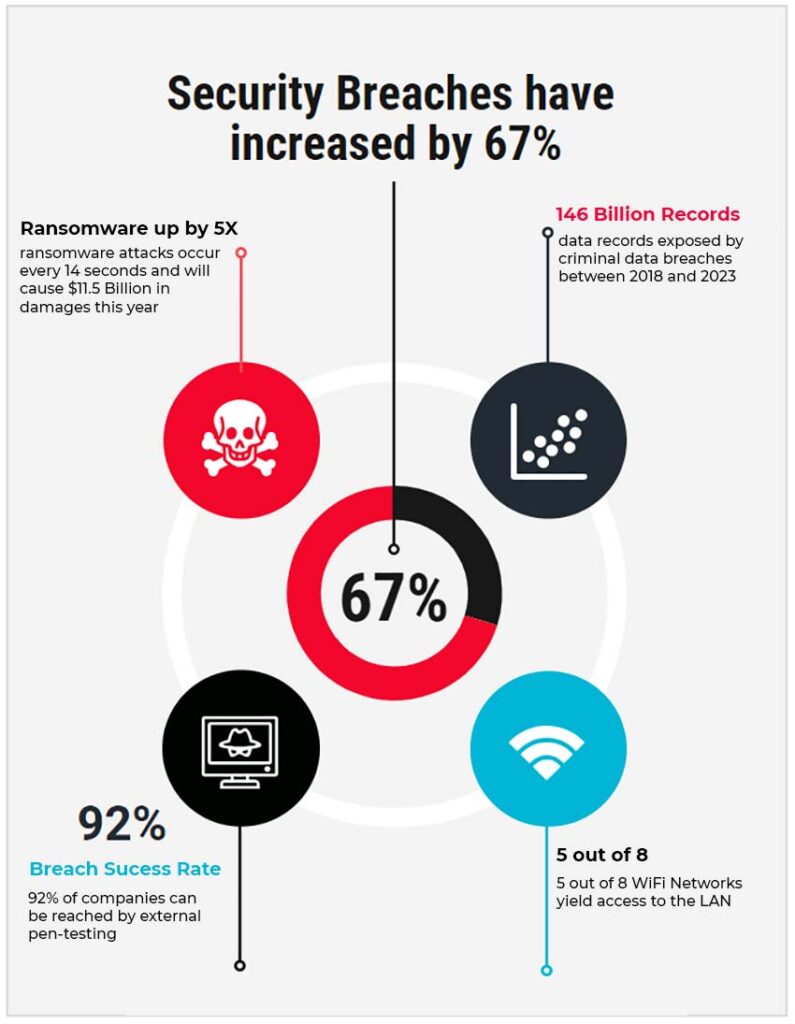
What are the Benefits of Using Penetration Testing?
- Some vulnerabilities can only be discovered through penetration testing.
- Security standards necessitate penetration testing.
- The most significant advantage of penetration testing is that it is risk-based. It aids in the identification of high-priority risks and the development of business-specific test cases.
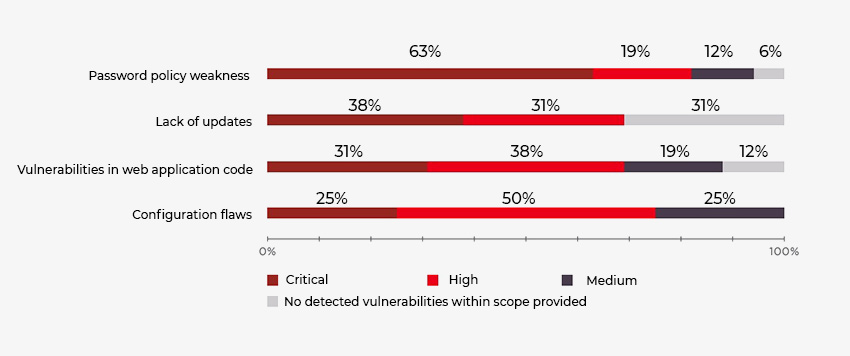
Source code review is a white-box methodology in which the code reviewer employs automated tools and a manual approach to identify security flaws in the given source code. Penetration testing is predominantly a black-box methodology in which the organization only provides the URL of the application under test. During a penetration test, the security analyst will typically begin by gathering information and then identify the system’s vulnerabilities. Later, the analyst will attack the system under test, attempting to penetrate deeper and deeper to identify additional security issues and assess the impact of the discovered vulnerabilities.
What are some of the Factors that’ll help you to determine the best suitable test for your development?
- Source Code reviews are generally more expensive than Penetration tests.
- Source Code requires more time and effort on your part you can’t just give an outsider a copy of the code and expect them to figure it all out on their own.
- Penetration tests do not require a lot of time or assistance from your team.
- You would need to hold hands and explain how the entire code was structured during the source code review. You’d want them to collaborate with your team to determine whether each finding is worth fixing, as well as to eliminate false positives and other misunderstandings.
- Intellectual Property and Confidentiality, as well as other legal concerns, are important, particularly for code reviews. You’re allowing an outsider to review the code, and while you want to be open to ensure a thorough review, you may be jeopardizing your secret sauce.
- Pen testers with extensive experience testing web portals are easy to come by. They will be familiar with the overall architecture and will recognize common functions and workflows, and they will be able to rely on out-of-the-box scanning and fuzzing tools to assist them in testing.
- A code reviewer must be competent with the language in which your app is written. They must be thorough and familiar with the frameworks and libraries that you use.
- If you use a lot of third-party code for which you don’t have a source, a penetration test is your only option.
- If you’re late in development, look for any high-risk exploitable vulnerabilities because that’s all you’ll have time to fix. This is where a lot of penetration testing takes place.
- It is preferable to choose a code review if you are in the early stages of development. Penetration testing doesn’t make a lot of sense, and a source code review can help the team get started on the rest of the code that needs to be written.
Conclusion
A source code review or a penetration test will not reveal all of the security errors in an app or even both of them. If you ask us which one to choose, we would say source code review if all other factors were equal. A review will require more time and effort, and it may not expose as many security bugs. But a source code review will provide more long-term value. Developers will learn more and faster, hopefully enough to identify and fix security issues on their own and, more importantly, to avoid them in the first place.
The type of security testing you already conduct on your own can influence whether a penetration test or a source code review is more beneficial.
Related Articles
-
A guide to choose the best dot net development company
Talking About A guide to choose the best dot net development company, In this smart age, where websites and applications are basic requirements of every business, people have started building
-
iPhone 6 Specs with New Business Opportunities for iPhone apps development
It’s time for a new Apple device and rumors are already floating in the mobile market about what this new device holds. There’s a lot of buzz and a lot
-
Airbnb: Business Model And Revenue Source
Airbnb has been around since 2008 and also has assisted travelers with finding a place to stay or find lodging during their trip. They’ve seen a considerable increase in popularity